When creating RedEye, we used our extensive experience and designed mechanisms that are extremely difficult for an attacker to bypass. When designing detection variants, we thought like advanced attackers, looking for the possibility of detecting both the presence of an IDS system and methods of bypassing its intrusion detection mechanisms.
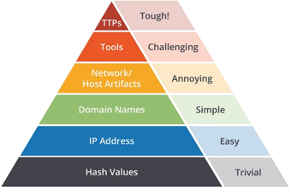
In searching for threats at the tip of the widely recognized so-called The Pyramid of Pain which contains information on how attackers (TTPs) and what tools they use. It is this information that is most in demand in threat hunting, i.e. proactive threat hunting. First of all, we implemented this knowledge in RedEye, thanks to which we have created a unique solution on the market for monitoring potential threats related to unusual behaviors in the network and the detection of advanced APT attacks (Advanced Persistent Threat).





